
Why is Physical Security Important?
Cyber security starts with Physical security, and is more than just walls and locked doors in the context of cyber security. It includes CCTV surveillance, security personnel, biometrics, and access controls. Because physical data theft of laptops, portable devices, media, and paper files is one of the most common security breaches. Having good physical security practices in place can often be all that stands between you and a data breach. Lets look at why cyber security starts with physical security.
In this article, we will outline physical security in the context of cyber security. We will have a look at the top ten best practices for securing your environment physically. Most of these you may think are common sense. However, it is astonishing how many reputable companies get these wrong and pay the price. We will also look at the types of physical threats there are. There are four areas that require controls to maintain robust physical security in an environment. We will outline what methods the attacker uses to physically infiltrate an organisation.
Physical Security Best Practices
Before you first turn the servers on, you should ensure that there are good locks on the server room door. Of course, the best lock in the world does no good if it is not in use. You need policies requiring that those doors are secure, and they should list who has authorised access.
Lock the server room
Locking the door to the server room is a good first step, but someone could break in. Someone who has authorised access could also misuse that authority. You need a way to know who goes in and out and when. A logbook is the most elementary way to accomplish this, but it has a lot of drawbacks. A person with malicious intent is likely to just bypass it.
Authentication systems
A better solution is to incorporate an authentication system into the locking devices. This means a smart card, token, or biometric scan requirement to unlock the doors. This then records the identity of each person who enters.

Video surveillance
Place a video surveillance camera in a location that makes it difficult to tamper with or disable. It should give a good view of persons entering and leaving and will supplement the logbook or electronic access system. Surveillance cams can monitor continuously, or they can use motion detection technology to record only when someone is moving about. They can also send email or text messages if they detect motion out of hours.
Secure devices
Remember, it’s not just the servers you have to worry about. A hacker can plug a laptop into a hub and use sniffer software to capture data traveling across the network. Make sure that as many of your network devices as possible are in that secure room. Alternatively, they may need to be in a different area, in a locked closet elsewhere in the building.
Bolt down hardware
Rack mount servers not only take up less server room real estate. They are also easier to secure. Although smaller than tower systems, they can easily be locked into closed racks and be bolted down. This makes the entire package almost impossible to move, much less to steal.
Secure unoccupied workstations
Hackers can use any unsecured computer connected to the network to access or delete information that’s important to your business. Workstations at unoccupied desks or in empty offices such as the front receptionist’s desk, are particularly vulnerable.
Disconnect and/or remove computers that are not in use. Lock the doors of empty offices, including those that are temporarily empty while an employee is absent. Equip computers that must remain in open areas with smart card or biometric readers. This will ensure that it’s more difficult for unauthorised persons to log on.
Both servers and workstations should have protection from thieves who can open the case and grab the hard drive. It’s easier to steal a hard disk in your pocket than to carry a full tower off the premises. Many computers come with case locks to prevent opening the case without a key.
Laptops and handheld computers pose special physical security risks. A thief can easily steal the entire computer, including any data stored on its disk. It may also include network logon passwords in the storage. If employees use laptops, they should take them with them when they leave or secure them with a cable lock.
Other considerations
Lock handhelds in a drawer or slip them into a pocket so they are on your person when you leave. Motion sensing alarms are also available to alert you when your portable moves. Full disk encryption and biometric readers can supplement physical precautions.
Backups
Don’t overlook the fact that some workers may back up their work on disks, USB keys, or external hard disks. If you allow or encourage this practice, be sure to have policies requiring that the backups be always secure.
Backing up important data is an essential element in disaster recovery. However, don’t forget that the information on those backup tapes, disks, or discs can be stolen. Many IT administrators keep the backups next to the server in the server room. They should be locked in a drawer or safe at the very least. Ideally, backups should be secure in an of-site location.
If you don’t want employees copying company information, you can disable or remove means of connecting external drives. Simply disconnecting the cables may not deter technically savvy workers. Some organisations go so far as to fill ports with glue or other substances to permanently prevent their use. However, there are software mechanisms that disallow it. Retro fit disc locks into drives on those computers that still have them, to lock out other diskettes.
Secure printers
Printers are often overlooked as potential security risks. However, many of today’s printers store document contents in their own on-board memories. If a hacker steals the printer, they may be able to make copies sensitive documents. Printers, like servers and workstations that store important information, should be in secure locations and bolted down.
Also, think about the physical security of documents that workers print out. Copies that don’t print perfectly may be just abandoned at the printer or thrown intact into the bin. It’s best to implement a policy of immediately shredding any unwanted printed documents, even those that don’t contain confidential information. This establishes a habit and frees the end user of the responsibility for determining whether a document should be shredded.
Remember that network security starts at the physical level. All the firewalls in the world won’t stop an intruder who can gain physical access to your network, so lock up as well as lock down.
Most physical security is common sense and can be improved greatly just by giving it a little thought and by implementing the right controls. For more advice about physical security or to book a physical security assessment with Sencode, contact us.
Frequently Asked Questions
Physical security is comprised of the tangible measures put in place to prevent the unauthorised physical access to business-critical systems. This can typically include, cyber awareness training, social engineering testing. Physical security is a broad term that encompasses people, hardware, software, networks, and data.
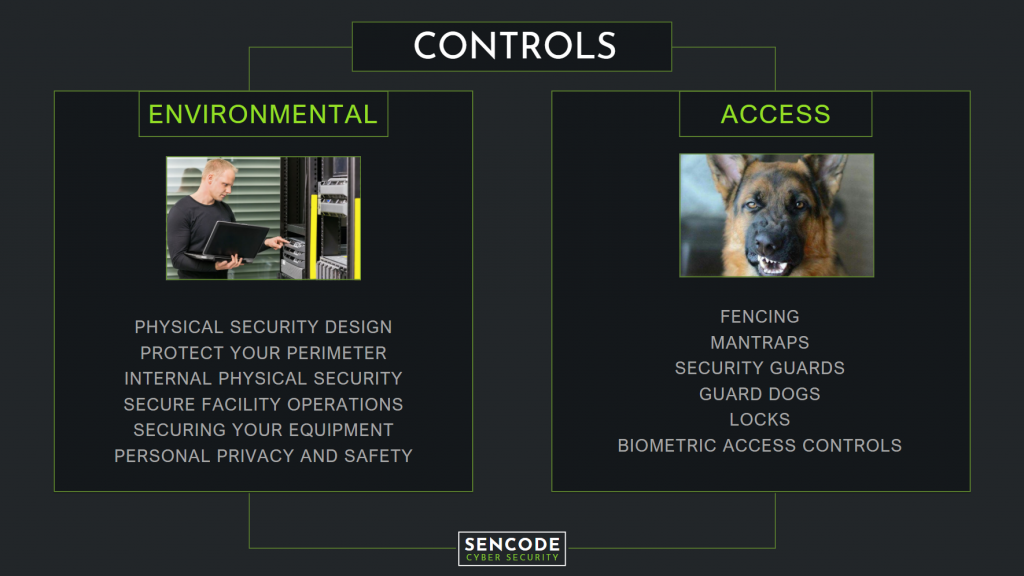
There are four categories of controls that can be implemented to improve the physical security of an organisation. Environmental Controls, Access Controls, Administrative Controls, and Technical Controls. More than just walls and locked doors, physical security controls include CCTV surveillance, security personnel, biometrics, intrusion detection systems, and many others.
Because physical data theft is one of the most common security breaches, having good physical security practices in place can often be all that stands between you and a data breach.
A variety of anti-tailgating strategies are available. Smart cards, turnstiles, security guards, PIN numbers, and man traps are all possible options. Which system is right for you is dependent on the specific entry point you want to secure, the layout of the entrance, the reason for controlling access to it, and the flexibility of your budget.
The answer to this is not necessarily a clear one. Ultimately it is up to the business owner how best to physically protect their assets, but whether this is taken on by a specifically employed security detail or delegated to the IT department should depend on the business type and what are considered to be the most valuable company assets.