Passwords are often the weakest part of an organisation’s or individual’s security. Often passwords are easy to guess, reused, or stored improperly, meaning a hacker with enough skill can gain access to your password and use it to compromise your accounts. This article covers the different ways a hacker might try to obtain your password and use it to attack you, alongside how password managers can help make your passwords more secure.
Reusing a password
If you reuse the same passwords, it’s only a matter of time before a hacker gains access to them. This is even true for long and complex passwords. This is because even the best passwords in the world are useless when the websites you visit store them insecurely. A website will usually store a hash of your password in a database (a unique value created from the characters). When you need to log in they simply re-compute a hash based on what you provided. If they match, they know the input you gave them is correct. But this also means if a hacker gains access to the website, they can crack your password’s hash. If your password is in a data breach, no matter how complex the password may be, it shouldn’t go back into circulation.
Once this happens to a password, it is commonly retrievable online or sold on the ‘darknet’ which allows hackers to simply search for someone they want to hack and get their information.
Weak Password?
Another simple win for a hacker is weak passwords or passwords based on the previous password. Around 10% of corporate passwords are a combination of the season/month and year or something simple like ‘password123’ or ‘qwerty000.’ These simple passwords are also dangerous because they enable a password spraying attack. This is where an attacker uses a small number of passwords to try to get into multiple accounts, but prioritises accounts with weak passwords.
This allows the attacker to discover which accounts they can access and use those accounts to gain more information or even hack an organisation.
Improper Storage
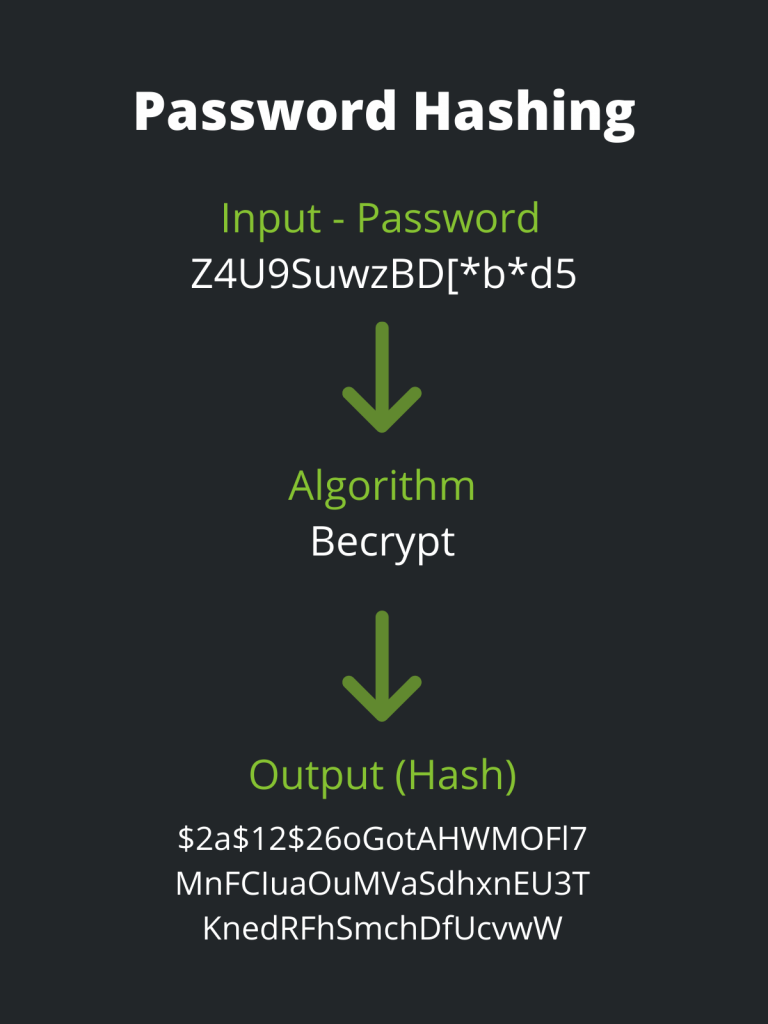
Improper storage does not only extend to people but also systems and organisation’s. If you write your passwords down, you should store them in a secure cupboard and create access controls to the key. Systems that store passwords often store a hash of them. If they are using a weak hashing algorithm such as MD5 or even no hashing algorithm at all, it can mean hackers will have access to all the passwords stored if there is a data breach on that system.
An attacker will have a significantly tougher time cracking hashes if you use an algorithm like bcrypt. This is due to the fact that they use slower hashing techniques. Because bcrypt hashes take longer to compute, an attacker will have a considerably tougher time breaking them. Salting passwords with a random string will also make them far more difficult to crack.
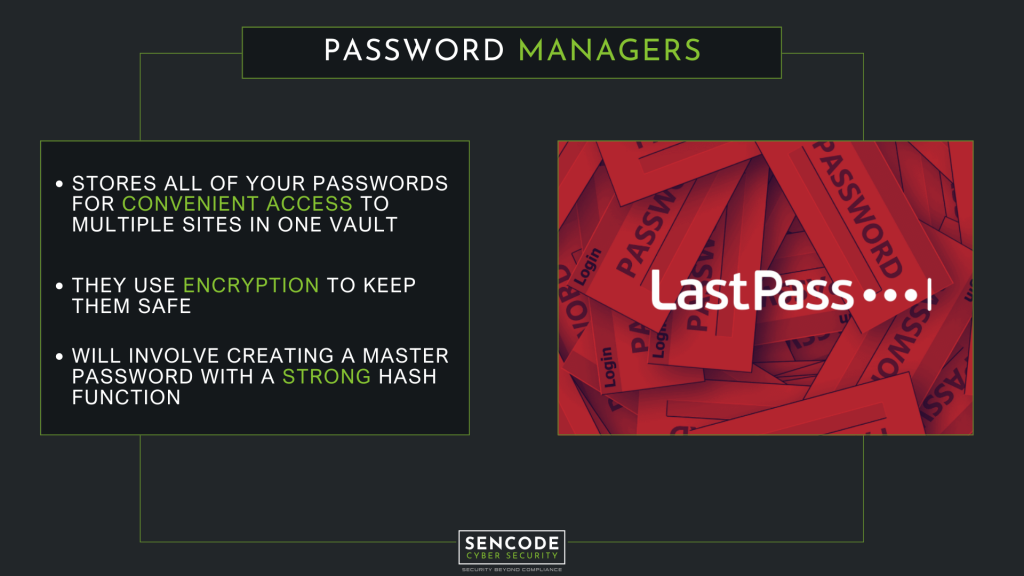
The solution – password managers!
Password managers can remove a lot of the risk inherent in passwords by providing unique, secure passwords. They store them in a way that cannot be accessed without the master password. Using password managers will not fix websites that do not store passwords correctly. They can, however, make sure that passwords discovered in a data breach are not used on other accounts. Thus, making the accounts more secure.
In conjunction with 2FA (Two-factor authentication) password managers can provide a significant upgrade in security for an organisation or individual. 2FA can work to ensure that only you can access your password manager, giving you an extra layer of security. Enabling 2FA on all of your accounts ensures that hackers will be unable to access them.
What if I do not want to use a password manager?
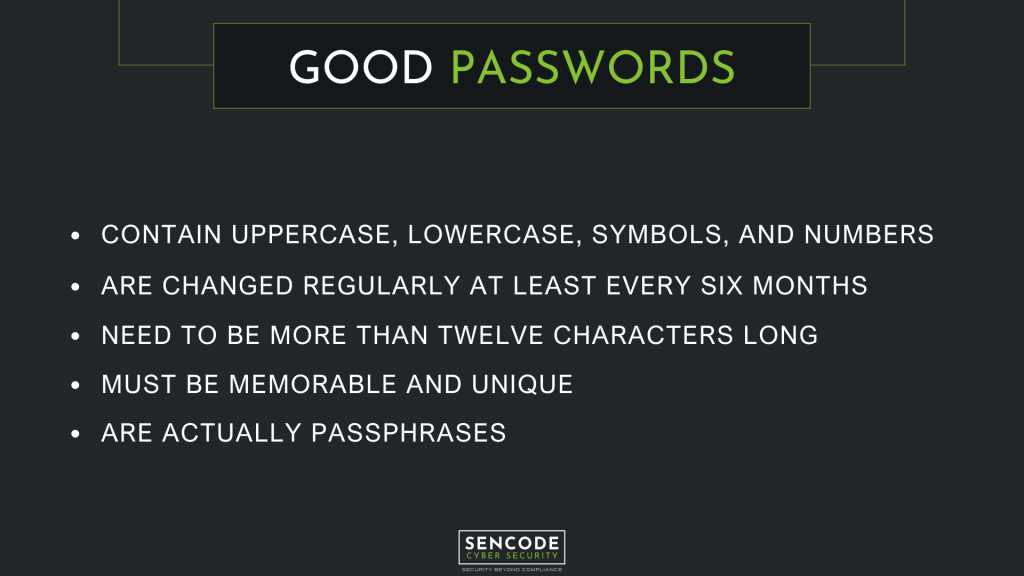
This is a personal choice, some people do not trust using password managers and see them as a single point of failure. If this is you, ensure you stick to the following when creating a password.
Frequently Asked Questions
Although password managers, like any other piece of software, can be hacked, the techniques used to encrypt and save passwords are typically regarded as secure. This implies that even if an attacker gained access to your machine or password manager, they would still require the master password to access any data stored. There could be problems with the encryption algorithms or implementation, but if that were the case, there would be far more serious cyber security threatsthan password access because passwords would be rendered meaningless.
Password managers are frequently security tested, and while they may have occasional vulnerabilities, the way they store passwords prevents them from being accessed with the master password. Password managers are not only secure, but they also make all of your other accounts more secure by eliminating password reuse, weak passwords, and improperstorage.
The top passwords of 2021 were the following:
– 123456
– 123456789
– qwerty
– password
– 12345
– qwerty123
– 1q2w3e
– 12345678
– 111111
– 1234567890