If the name doesn’t already sound strange enough, wait until you see what you can do with Google Dorking. Before we dive deep into how we can use Google Dorking. We must first look at search engines themselves.
What is a search engine?
A search engine can be thought of as a behemothic database, however, it is far more sophisticated than that. A search engine will return a list of results that are the most relevant to the user’s search. On the Internet nowadays, there are a plethora of search engines, each with its unique set of capabilities and features. Google is by far the most popular search engine, although several other search engines exist that answer billions of user queries worldwide. DuckDuckgo, Bing, Baidu just to name a few.
How does a search engine work?
Many search engines present the results based on their importance because huge search engines include millions, if not billions, of pages. Various algorithms are routinely used to determine this relevance.
Search engines work by crawling (also known as spidering) a page, then processing the contained data. These days that involves complex processing, which is not surprising considering the vastness of the internet in 2021. The data will be processed and analysed to strip out content, keywords, and other data which the search engine deems relevant.
Google Dorking
Now we have learned a little about search engines, let’s take a look at Google Dorking. But what is it exactly? Google Dorking is essentially a searching strategy that allows hackers to easily acquire access to data that businesses or individuals did not intend to make public. TLDR: “Google Dorking is essentially a useful hacking shortcut for locating systems and data of interest.”
Okay, let’s jump into some Google Dorking commands. We will keep it simple to start with.
Using quotation marks – “something”
We can use quotation marks to limit down our search query, for example. Everything between these quotation marks will be interpreted as exact by Google, and it will only provide results for the exact term entered. This is the most basic example of Google Dorking that can be achieved.
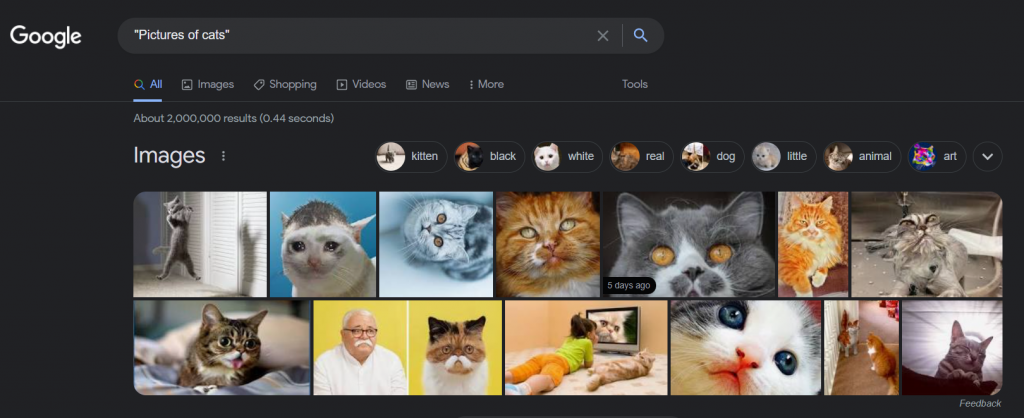
Okay great. we have some pictures of cats. Let’s move on to some more interesting Google Dorking commands.
Using the “site:” operator
We can use the site operator to narrow down our query to only the website we specify. Using this Google Dorking command, we should only see the site queried alongside any other words we specify after the command. Let’s look at an example of this Google Dork.
Query - site:pastebin.com passwords
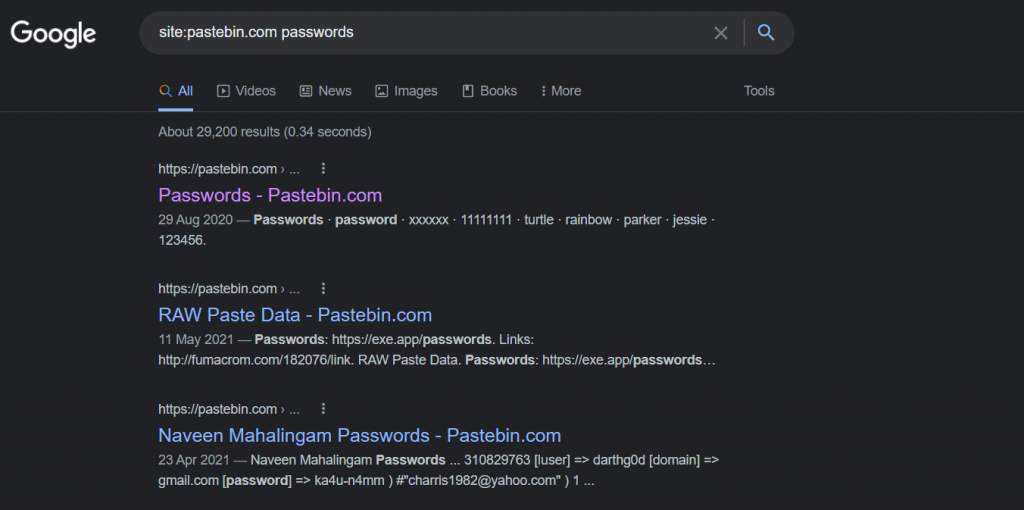
Fantastic, we have a more interesting result than our previous cat images.

Using the site: and intext: operators.
The site operator is great and all. But using it alongside ‘intext:‘ will reveal more juicy information. What does ‘intext:’ do exactly? Intext will search the web page content for whatever you type in.
Query - intext:"SECRET_KEY=" site:pastebin.com
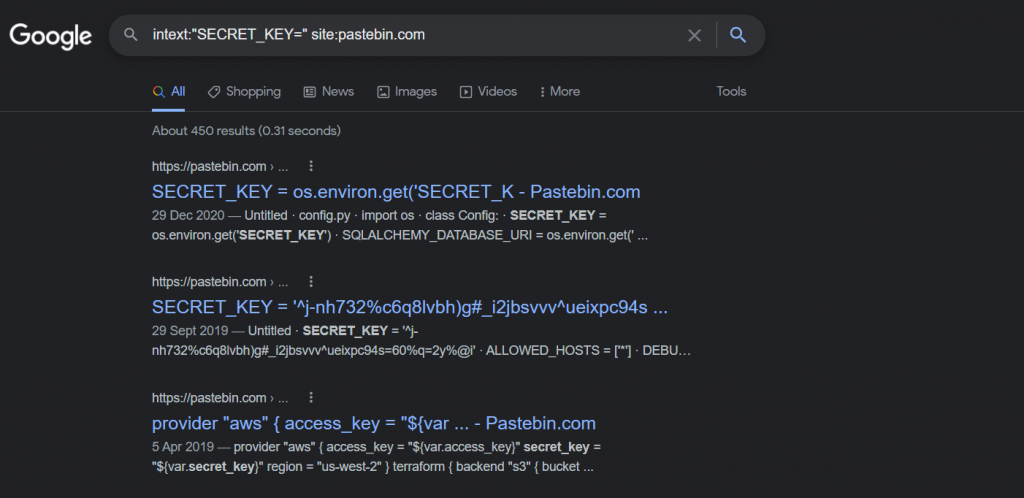
Great stuff, we have told google to find all indexed pages on pastebin.com and return all items which contain the text “SECRET_KEY“. Using a google dork.
Google Hacking Database
It’s not possible to write a blog post about Google Dorking without mentioning the Google Hacking Database. This database has been compiled for several years by security professionals who take their Google Dorking seriously.
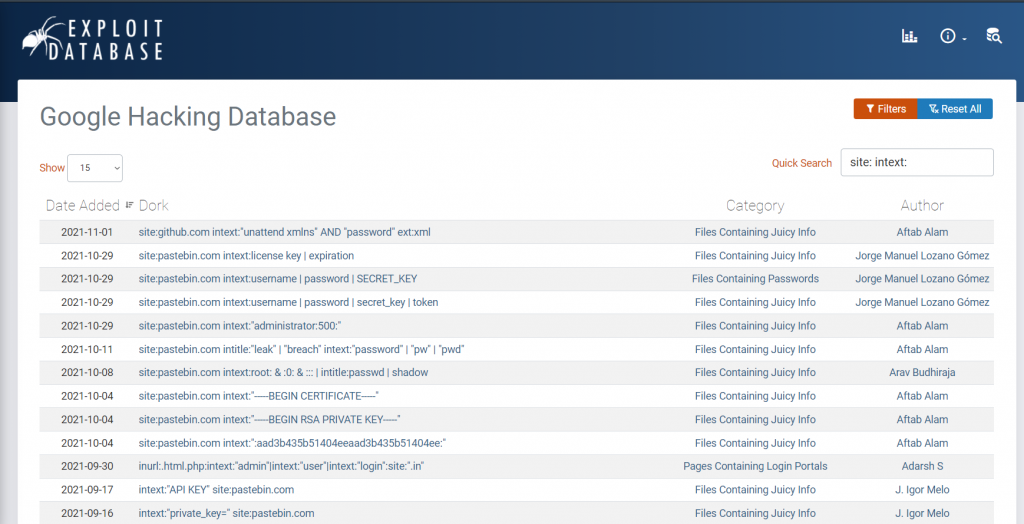
As of this writing, there are 7,064 google dorks in the Google Hacking Database. Which is more than enough for any Google Dorking enthusiast. The Google Hacking Database can be filtered to search for very specific dorks. It lists several categories, “Vulnerable Files“, “Web Sever Detection“, “Files Containing Juicy Information” just to name a few.
Google Dork Commands
| Operator | Description | Example |
|---|---|---|
| site | Will display a complete list of all indexed URLs for the supplied domain and subdomain. | site: sencode.co.uk |
| allintitle | Will only show pages with titles that contain X characters. | allintitle: “Security Beyond Compliance” |
| allinurl | Will only display results that have all of the provided characters in their URL. | allinurl:sencode |
| filetype | Used to find any type of file extension; for example, if you wanted to find our ‘Owasp Top 10 Flash Cards‘. | filetype:pdf owasp top 10 flash cards |
| inurl | This is identical to allinurl, however it is only usable for one term, such as inurl | inurl:sencode |
| intitle | This operator will only return keywords inside the title. | intitle:sencode |
| inanchor | Will only return exact anchor text used on any links. | inanchor:”web application penetration testing” |
| intext | Will only return pages which contain certain characters or strings inside their text | intext:”Owasp Top 10 Flash Cards” |
Who uses Google Dorking?
Google Dorking is frequently used by computer security experts, cyber criminals and researchers. It is also used during the reconnaissance phase of penetration testing.
Frequently Asked Questions
Google Dorking is a search tactic that makes it simple for hackers to gain access to information that organisations or individuals did not intend to make public. It’s a handy hacking shortcut for locating relevant systems and data.
Different laws apply depending on where you are in the world. Using Google Dorking is probably not against the law, but accessing the URL behind that indexed page might be. When you click one of the links, you’ll be taken to a resource that may or may not have been made intentionally available. Local laws that apply to that system may record and/or protect the action.