Expert CREST-Accredited Penetration Testing
Security Beyond Compliance
Discover quality security assessments from certified professionals. Our services are designed to help companies meaningfully improve their security. Get a quick, no-obligation quote today.
Penetration Testing Service
Secure your digital assets today. Defend your valuable data and services from attackers with our comprehensive and proactive CREST Penetration Testing.
Cyber Security Assessments
Whether you need a full Red Team Assessment or a Corporate OSINT Assessment, our team of security experts has you covered. Our team are experts at tailoring our services to your requirements.
Build Cyber Resilience Now
On-site or online cyber awareness training from experienced instructors. Empower your staff and protect your business from within. Tailored awareness training is available on request.
Build a Human Firewall

Why Sencode?
Sencode is a multi-award-winning company with end-to-end ownership of everything we do. We specialise in advanced CREST penetration testing services, social engineering, and cybersecurity training. Additionally, we offer a free retest and carbon offsetting for each penetration test we conduct. Our testing includes personalised remediation for the diverse sectors we serve.

Introducing Sencode Portal
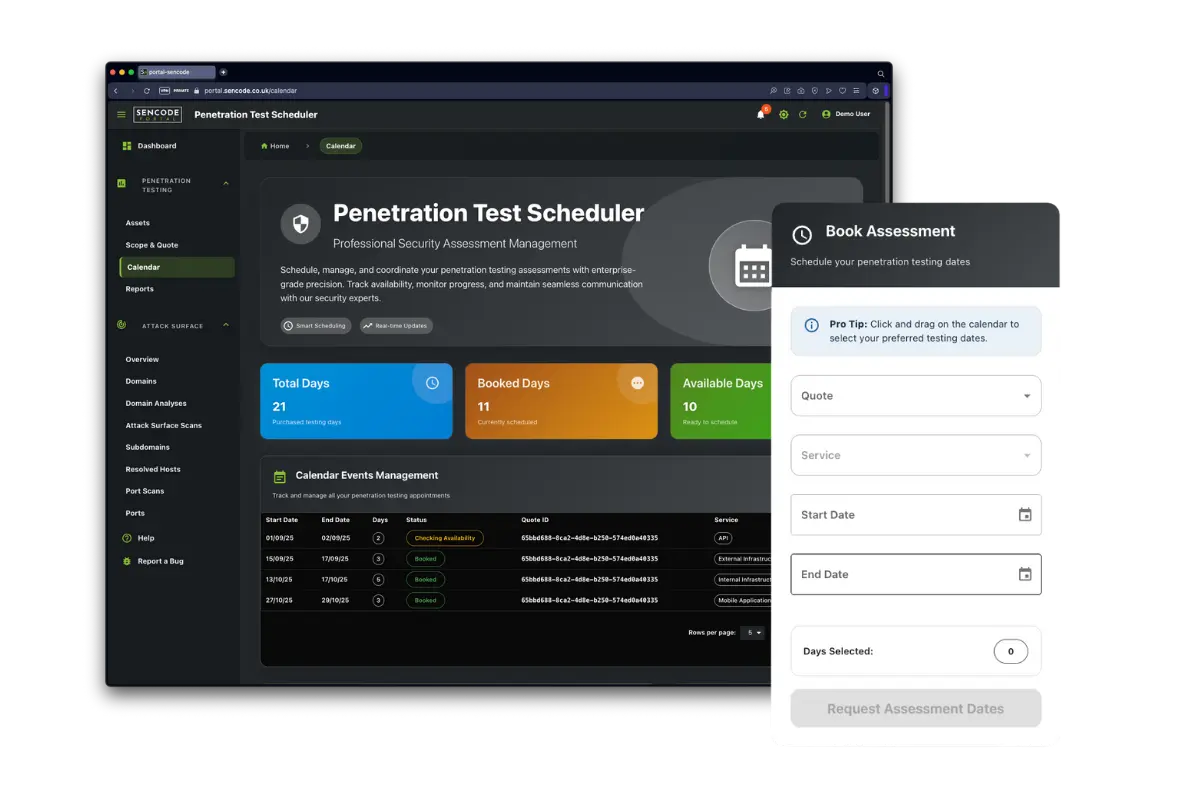
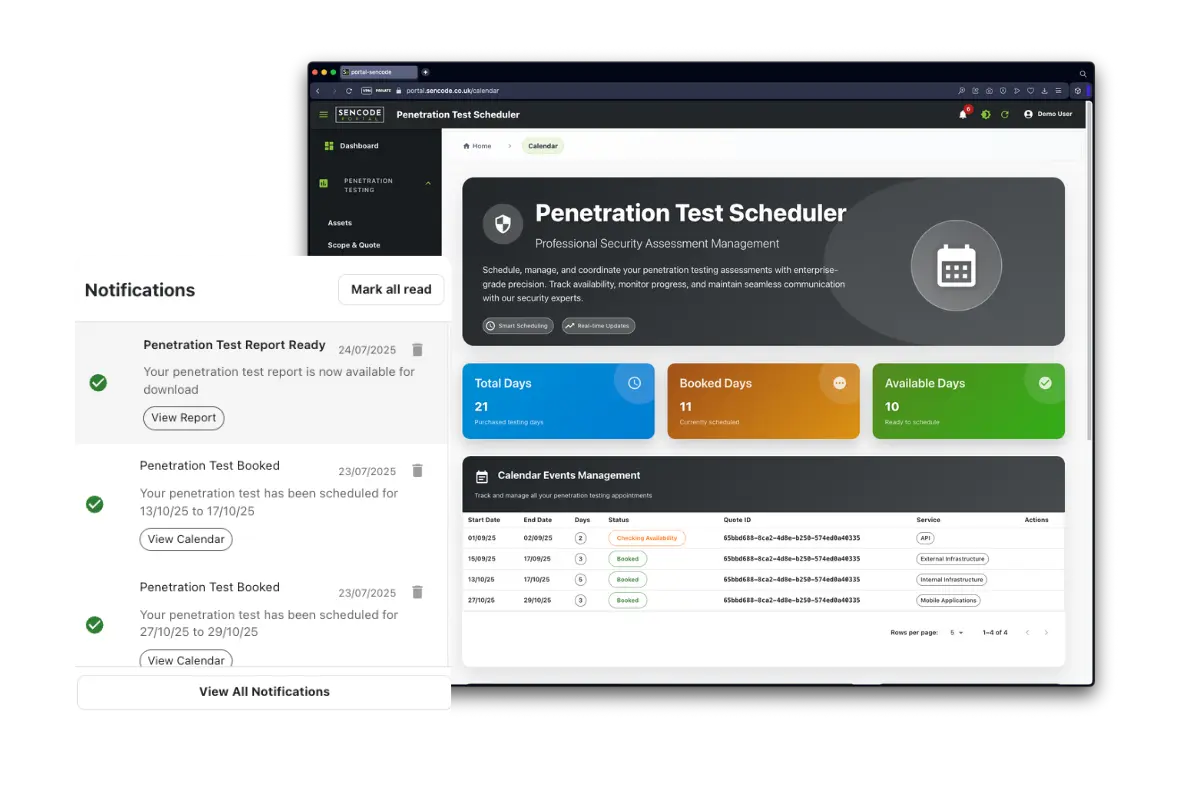
Penetration Test Scheduler
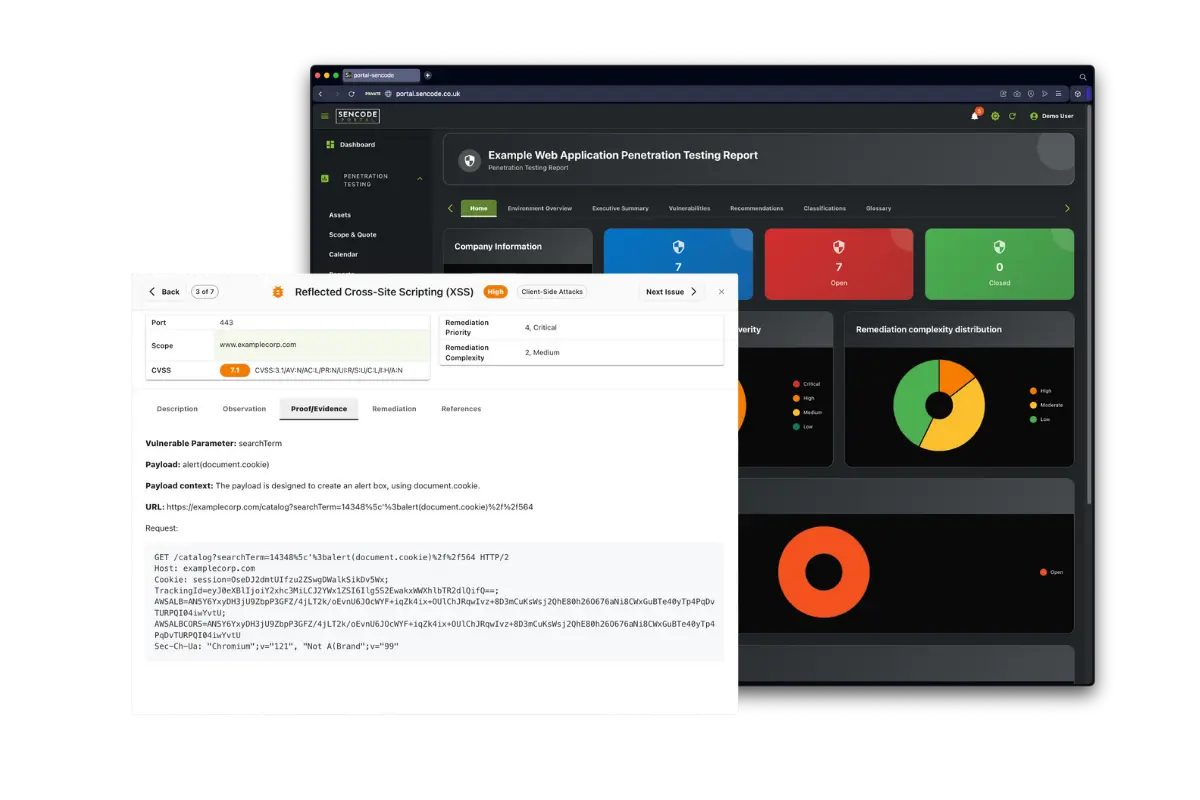
Penetration Test Reports, Delivered.
Security Classifications
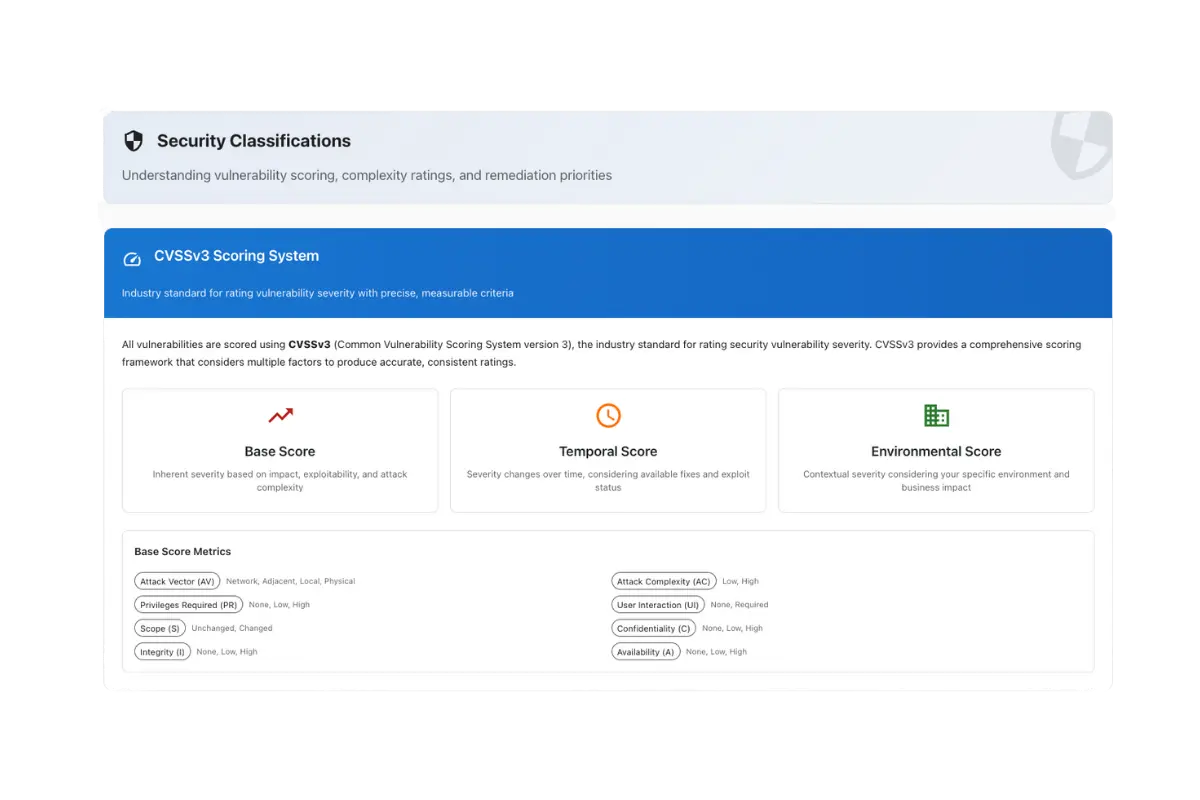
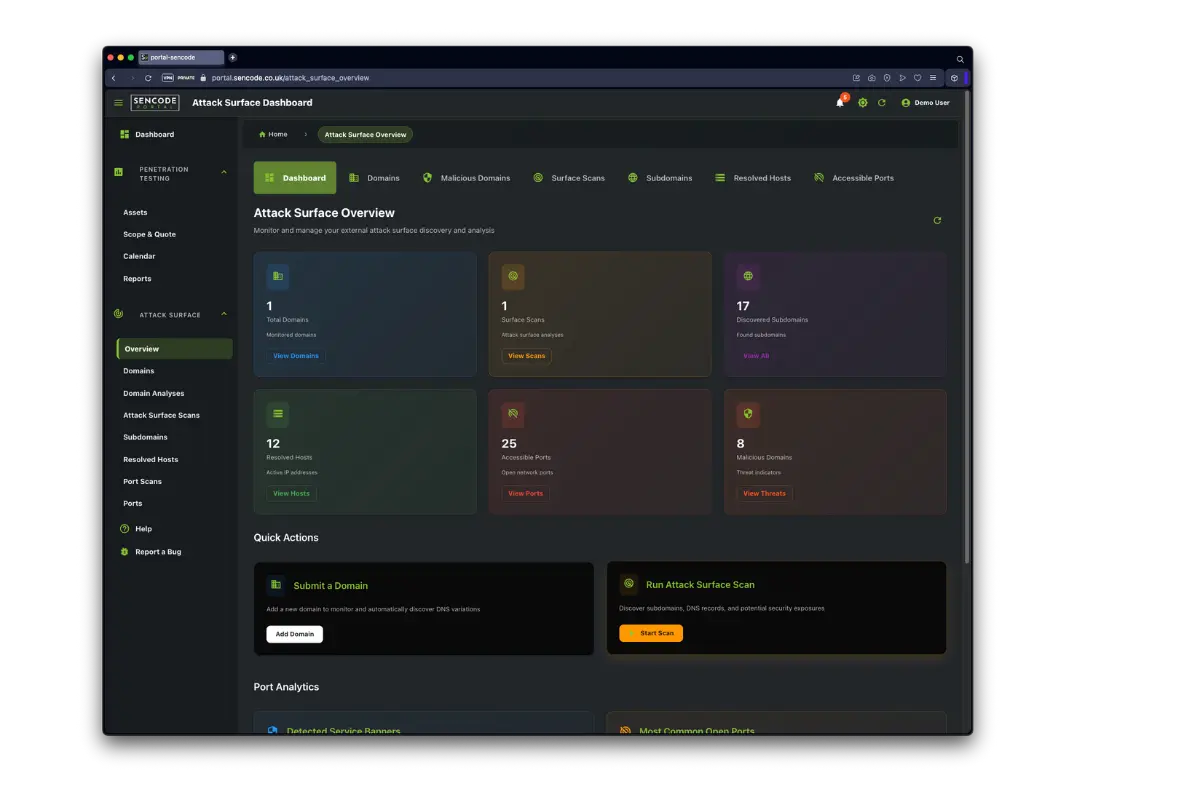
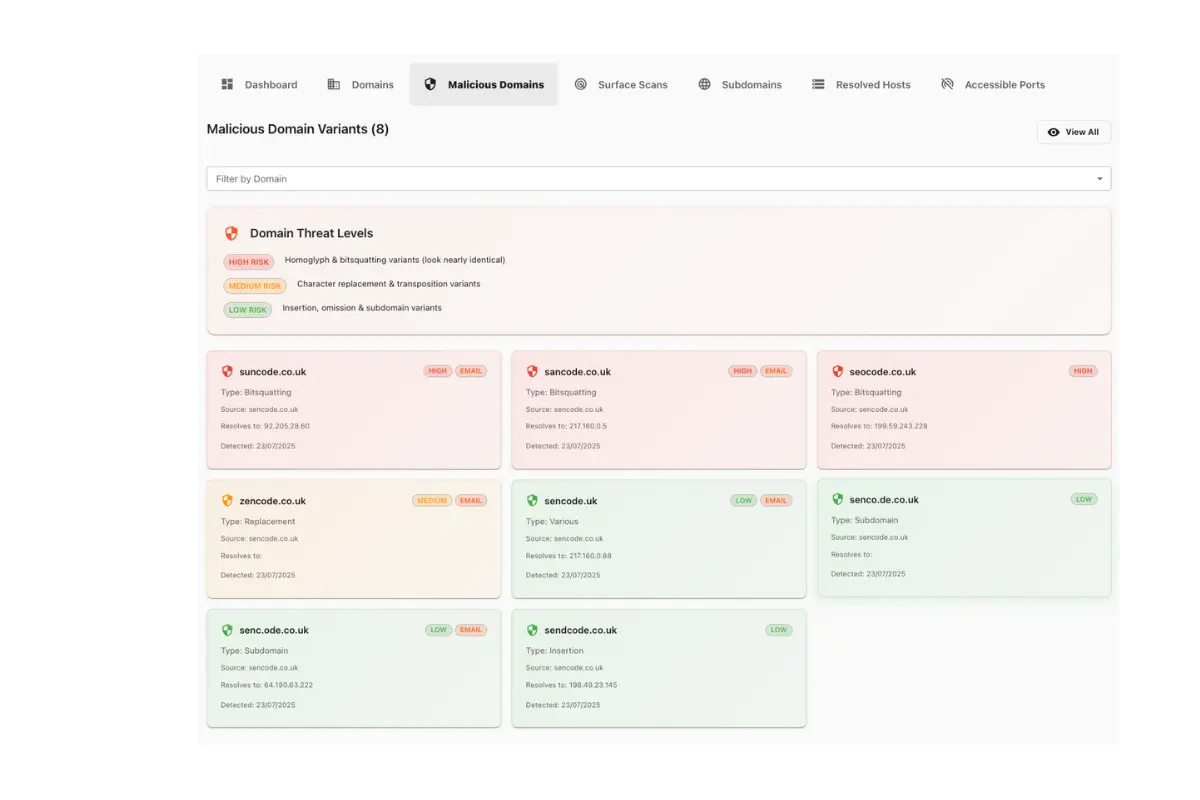
Attack Surface
Trust Our
Comprehensive Reporting
Here at Sencode Cyber Security, we believe that reports should be written for human beings, not robots. We produce comprehensive reports and avoid unnecessary technical jargon.
Security Professionals
All of our security testers hold industry-leading certifications, such as the Offensive Security Certified Professional (OSCP) and CREST.
Quality Training
We ensure that complex concepts are explained using practical and simple terminology, making them easier for non-technical staff to understand and gain the perspective of a threat actor.
Constant Innovation
Our mission is to provide state-of-the-art security services and products that are user-friendly and relatable to our clients so that they are empowered to improve their security posture.
Contact a consulting team member by phone, email, or pigeon post. We will then discuss whether we can help you and arrange a scoping meeting to discuss your requirements.
In the scoping meeting, our team will discuss your requirements in further detail. Our team will ask questions in regards to the following:
Our expert consultants will discuss and finalise which digital assets you need testing in the scoping meeting. Based on the requirements, we will then assemble a project proposal and quote and agree on a schedule for conducting the security assessment. Our proposal document will include the following information:
The Penetration Testing starts. A member of our Penetration Testing team will liaise with a member of your company throughout the entire testing process. You will be the first to know if we have any questions or concerns. Our testing team will be on hand throughout the penetration test lifecycle to answer any questions or concerns. Our tester will:
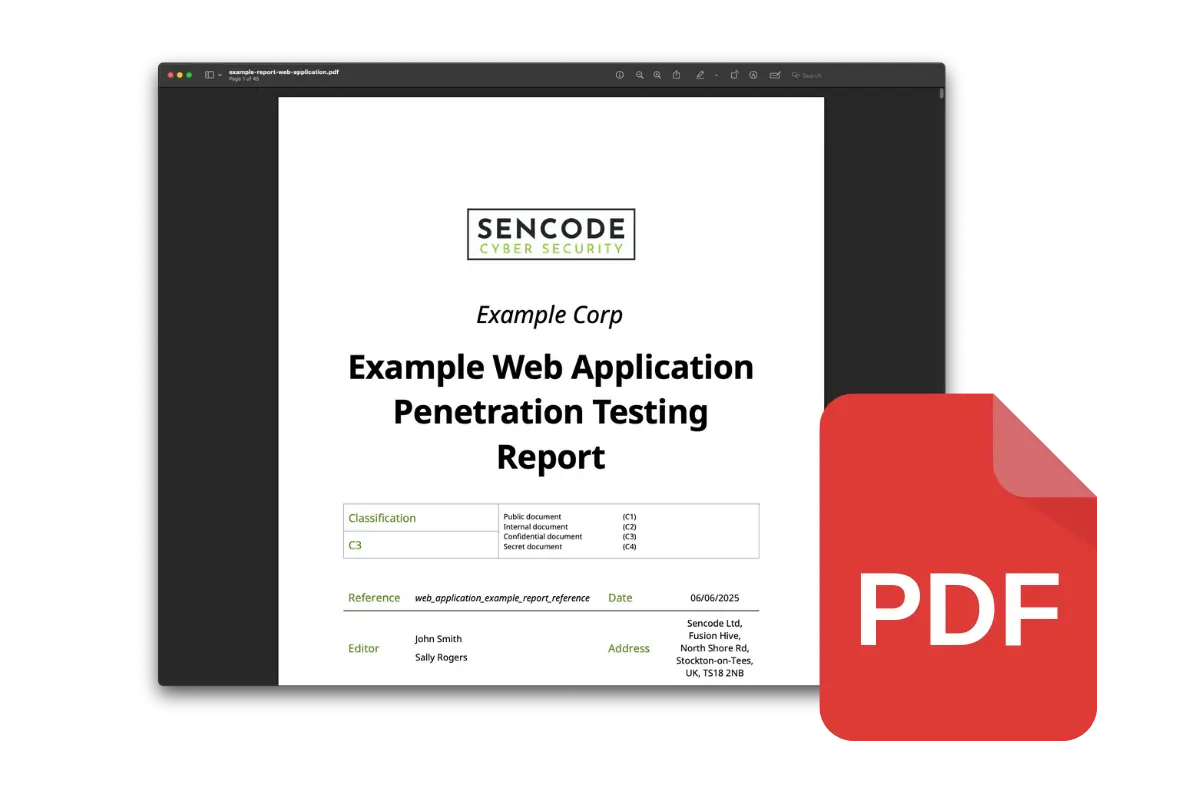
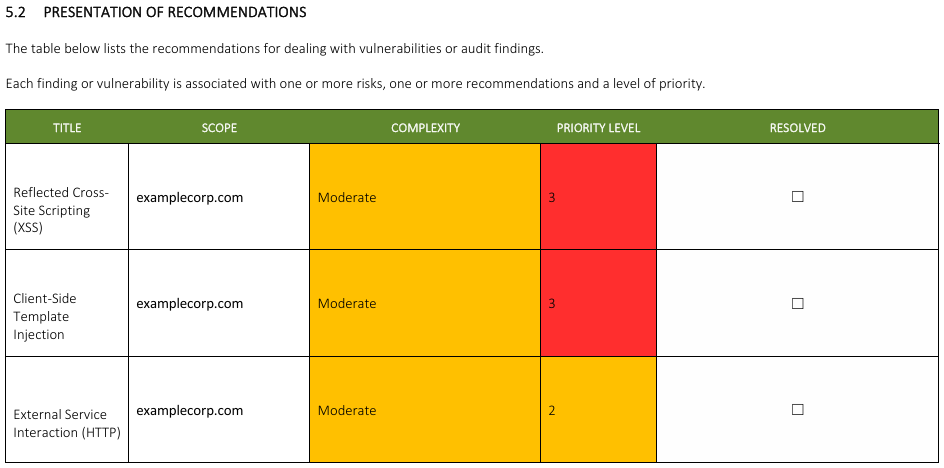
A Penetration Test is useless without a well-written report. Our reports are written in plain English, concise, and thoroughly documented. The Penetration Test Report is typically furnished within 5 days after the testing phase is complete. If you are interested in seeing an example report, please contact our team.
Each report details the following:
At Sencode, we offer free retesting for every Penetration Test we conduct. You fix the issues; then we will verify they can no longer be exploited by an attacker. Our team will arrange a mutually suitable time to conduct the retest, after the remediation efforts have taken place. Our tester will follow these steps:
Our clients receive a testing certificate that can be shared with partners and customers, showing that their company takes security seriously. The certificate and document are designed to be easily digested by third-party suppliers, the document removes the technical details and can be safely distributed.
The Security Testing Certificate is available on request, after the retest has been complete. The security certificate shows:
Get in touch for a consultation.
Contact a consulting team member by phone, email, or pigeon post. We will then discuss whether we can help you and arrange a scoping meeting to discuss your requirements.
In the scoping meeting, our team will discuss your requirements in further detail. Our team will ask questions in regards to the following:
CREST-Accredited Penetration Testing Services
Web App Penetration Testing
You can ensure the security of any online web application, whether internal or public-facing, by conducting comprehensive penetration testing. Our skilled testers follow the OWASP guidelines so that, while simulating an attacker’s behaviours, they may find security problems in your application using an established framework.
Network Penetration Testing
Led by expert penetration testing consultants. Our comprehensive Internal and External network infrastructure assessments help build resilience and improve the security posture of your corporate environment.
VAPT Testing
Explore comprehensive Vulnerability Assessment and Penetration Testing (VAPT) to safeguard your digital assets from vulnerabilities and cyber threats. Ensure security and regulatory compliance now.
Mobile Penetration Testing
Perform static and dynamic analysis of a mobile application for security vulnerabilities. Our mobile application tests ensure the security of any mobile app to the OWASP-MASV Standard alongside our custom methodology.
Cloud Penetration Testing
Verify the security of your cloud infrastructure, whether it’s hosted with AWS, Azure, GCP, or any other cloud platform. Our Cloud Penetration Test helps safeguard cloud infrastructure from hackers before they can act.
API Penetration Testing
Guard your API against attacks and misuse with an API Penetration Test. Whether internal or external, we will establish the security of an API and all of its endpoints, leaving no room for it to be exploited.
Our Penetration Testing Reporting
Key Cyber Security Statistics
Types of Cyber Security Services
Microsoft Cloud Security Review
A comprehensive analysis of your Microsoft Azure infrastructure, focusing on identifying and addressing security vulnerabilities and misconfigurations to enhance cloud security.
AWS Cloud Security Review
A detailed evaluation of your AWS environment aimed at uncovering potential security risks and ensuring compliance with best practices and policies.
Red Team Assessment
An advanced, full-scope simulation mimicking real-world cyber attacks, designed to test and improve the effectiveness of your entire security posture.
OSINT Assessment
Gathering and analysing information from publicly available sources to identify potential vulnerabilities and threats in your organisation’s digital footprint.
Testimonials
Huler
Trinity College Dublin
Diversity and Ability
Verve Group
Pip Studios
Home Group









Explore Our Downloadable Resources
Read the latest from our Cyber Security Blog
Contact us
Get a free, no-obligation quote from one of our expert staff.
This site is protected by reCAPTCHA and the Google
Privacy Policy and Terms of Service apply.






