Definition
Web application security testing is a rigorous practice designed to identify, analyse, and rectify vulnerabilities in web-based applications. This process involves the use of a comprehensive set of tools and methodologies to evaluate the safety and integrity of the web application. It encompasses practices like penetration testing, vulnerability assessments, and code reviews. The primary objective of web application security testing is to thwart potential cyber threats and ensure robust application performance in a secure digital environment.
Understanding the basics of web application security testing
Web application security is fundamentally about implementing protective measures to guard against threats to your digital platforms. This involves a process called security testing where the system’s vulnerabilities are identified and subsequently remedied. This process often involves website pen testing and web application penetration testing.
Why is web application security testing important?
A strong web security testing regiment includes a wide range of tools and processes in order to protect the users of any website. This often includes:
- Code security reviews – via the use of automated tools and manual assessment in order to find software and logic vulnerabilities within development and the codebase of the service.
- Regular Penetration Testing – to detect logic flaws and find security vulnerabilities that may have been missed by the developers of the application and meet regulatory requirements.
- External Vulnerability Scanning – to highlight outdated software components as soon as they appear.
- Information Security Audit – Looking at the policy or GDPR requirements of an application and the security of any data collected by the service and how it is used.
With web applications being a top target for cybercriminals, web application security testing becomes indispensable. Let’s take a look at some examples of large breaches which involved lax web application security.
WooCommerce Leak (2021)
In 2021, WooCommerce, a widely-used ecommerce plugin for WordPress, was found to have multiple vulnerabilities, including susceptibility to SQL injection attacks. These unpatched security flaws put data from 5 million websites at risk of being stolen. The incident underscores the importance of regularly updating and patching software to protect sensitive data.
The Cambridge Analytica Scandal (2018)
In 2018, the political consulting firm Cambridge Analytica exploited a vulnerability in Facebook’s API to access the personal data of millions of users without their consent. This breach highlighted the urgent need for better data privacy measures and stricter access controls. Facebook came under heavy scrutiny and was slapped with a $5 billion fine by the U.S. Federal Trade Commission for violating user privacy.
Strava API Breach (2018)
Strava, a fitness tracking app popular among military personnel, experienced a significant data breach in 2018 due to poorly designed API security. The breach exposed 3 trillion data points, covering 1 billion activities worldwide from January 2015 to September 2017. Among the exposed data were global heatmaps of military bases, posing a serious security risk. The incident highlights the need for robust API security, especially when sensitive locations are involved.
Both of these cases emphasise the critical importance of cybersecurity measures, not just for protecting individual user data, but also for safeguarding sensitive information that could have broader implications.
What are the common web application security testing tools in 2023?
Several tools are used in web application security testing, which include:
- Burp Suite Pro: A comprehensive collection of tools and metadata for testing websites, including features for SQL injection and side channel attacks. Burp suite is the defacto standard for penetration testing and bug hunting, this is due to the large volume of unique testing tools that are built into the suite, alongside the extendibility of the software with extender tools. (This is by far the main tool used by a web application security tester)
- Metasploit Framework: Simplifies the process of exploiting vulnerabilities with a user-friendly command line interface, session management, and a database of exploits. Metasploit contains a plethora of unique modules that can come in handy when testing web applications.
- Nuclei: Nuclei is used to send requests across targets based on a specific template defined by the user, leading to less false positives and providing fast scanning on a large number of hosts at the same time. Bug Bounty experts used Nuclei to test for specific vulnerabilities in a range of in-scope targets.
- Nmap: Despite being slow, Nmap is considered the best port scanner, providing essential features for reconnaissance with the Nmap Scripting Engine (NSE).
- Hashcat: Known for its speed, Hashcat can crack almost any password with appropriate resources. It offers various options and tweaks for password cracking, making it highly versatile. If a tester manages to obtain a hash during the assessment, Hashcat could be used in an attempt to crack it.

These tools assist in various tests such as web app penetration testing, the primary goal being to expose and patch vulnerabilities within the web applications.
The web application testing process
To conduct a test for a client, there are certain processes and preparations that need to be undertaken. This might seem daunting to some, but it shouldn’t be a cause for concern. In examining the testing process, the first step involves agreeing on a scope between the company, Sencode, and the client. The scope outlines the specific areas of the web application that are within the parameters of testing, from either an unauthenticated or authenticated perspective. The definition of scope provides test guidelines and serves as the starting point for the engagement.
Next, a tester analyses the application in order to understand its process flow. In doing so, the tester will identify all potential attack vectors present in the application. Following this discovery phase, the tester will actively begin to attack the application, employing numerous tools and methodologies, such as OWASP, to evaluate the web application.
The tester will be on the lookout for web application flaws such as SQL injection, cross-site scripting, and external entity injection. These vulnerabilities are commonly observed in web applications. The tester will categorise and evaluate these findings, illustrating the risk posed to the application during the test. It is not uncommon for a tester to chain several vulnerabilities together in order to increase the overall risk of the identified issues. This is especially common with authentication-based vulnerabilities, alongside chaining XSS with session management misconfigurations.
Different types of web application security testing
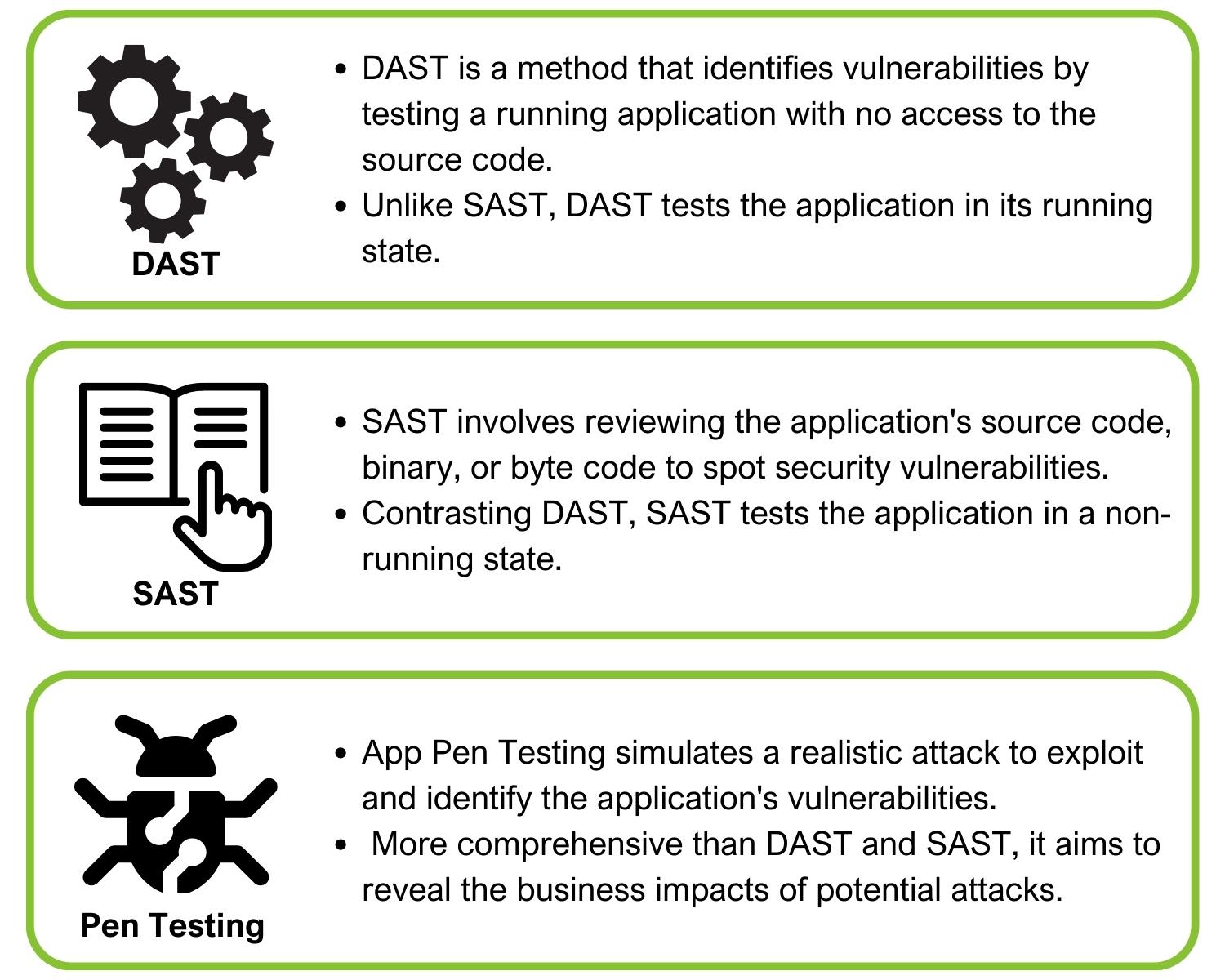
Web application security testing ranges from Dynamic Application Security Testing (DAST) and static Application Security Testing (SAST) to Application Penetration Testing. These tests ensure comprehensive checking for vulnerabilities covering both code-level issues and application-level penetration threats.
Dynamic Application Security Testing (DAST) is a security testing methodology that checks an application dynamically while it’s running, mainly focusing on exposing potential vulnerabilities that may exist in the running environment. It simulates attacks against an application and analyses responses to find security flaws. Unlike static application security testing, which analyses the app’s code, DAST tests the app’s functionality and behaviour in real-time scenarios, identifying security threats and weaknesses that could make it susceptible to attacks.
Static Application Security Testing (SAST) refers to a type of security testing that analyses an application’s source code, bytecode, or binary code for security vulnerabilities. Unlike Dynamic Application Security Testing (DAST), it does not require the application to be running. SAST can detect flaws, identify insecure coding practices early during the software development life cycle (SDLC), and provide precise information to fix the reported issues.
Application Penetration Testing (App Pen Testing) is a targeted process of simulating cyber-attacks on an application to examine its security strength. Unlike DAST or SAST which scrutinise the application while running and the source code respectively, App Pen Testing is an exploratory method where the tester actively manipulates the application to find exploitable vulnerabilities. It is a vital part of a comprehensive security testing strategy that supplements other methods like DAST and SAST, to ensure the most secure application environment possible.
Conclusion
Web application security testing is an undeniably integral part of maintaining the security integrity of web applications. Mastering its nuances can offer cyber-security professionals an edge in the industry and present web application owners with peace of mind in protecting sensitive data.
The increasing threats to web applications put the onus on every professional to understand the need for robust web application security testing. If you have a requirement for Web App Pen Testing contact Sencode.
Frequently Asked Questions
The restrictions placed on a website’s development by time, money, and skill can lead to several vulnerabilities being left unfixed. Often the only way to discover these vulnerabilities is to have an external party check. Web application penetration testing is frequently used to highlight vulnerabilities any web application may have.
Companies that hold personal information on their users are legally responsible for storing and protecting that information. Failure to do so by not actively checking or security issues with an application can lead to severe fines by the ICO and can lead to lawsuits being brought against them by the people impacted if there were to be a data breach.
Web application testing has a lot of cross-over with API testing but also exposes the tester to a much deeper attack surface, often involving a much more diverse selection of attacking techniques. As with every type of testing, the first step is discovery. This includes finding which parts of the application can be tested, and what technologies are being used (.NET,PHP,Angular for example).
Once this has been completed, we can cater our attacks to the specific website technologies being tested. We will test for security vulnerabilities such as XSS, SQLi, OS command injection, access control violations and many more.
Vulnerabilities can be chained together to create security issues with a higher severity. How can vulnerabilities be chained together? Take this example:
“During the testing we discovered the forgotten password function is vulnerable to username enumeration due to verbose responses. Account lockouts were not present on the system. Therefore we were able to chain these vulnerabilities together to compromise a large number of user accounts.”