A replay attack poses a significant threat because they can lead to unauthorised access and execution of operations within a network. The attacker essentially eavesdrops on a secure network communication, captures authentication protocols, and reuses them to trick the system into thinking that a new request is legitimate. This type of attack exploits the fact that some authentication systems do not have measures in place to distinguish between legitimate and fraudulently reused credentials.
Tools such as ‘ntlmrelayx’ from the Impacket suite can be used to perform relay attacks, which are a variation of replay attacks. In a relay attack, the attacker intercepts credentials and relays them to another service to authenticate as if they were the victim. Impacket’s ‘ntlmrelayx’ tool is particularly effective against networks using NTLM (NT LAN Manager) authentication. An attacker can relay NTLM authentication sessions and execute arbitrary code, gain elevated privileges, or access restricted resources.
The continuous development of penetration testing tools such as Impacket and the ever-evolving threat landscape mean that network and security professionals must remain vigilant, implementing comprehensive measures against such attacks.
To combat a replay attack, security mechanisms such as the use of nonces (random numbers used only once), timestamps, session tokens, and challenge-response authentication are employed, which can help detect and prevent replayed data packets. Secure communication protocols, such as Transport Layer Security (TLS), also include measures to protect against replay attacks.
Example of a Replay Attack
Replay attacks can take significant knowledge and expertise to configure, and you should always have the appropriate permissions to execute such an attack. Ensure you have explicit permission to perform these actions on any network. Unauthorised use of these tools is illegal and unethical.
This example involves using Responder and then using ntlmrelayx for relaying the captured credentials. The following is a step-by-step guide to setting up such an environment, focusing on the Responder tool to capture NTLM hashes and ntlmrelayx to relay these hashes to a target system. We will also utilise crackmapexec in order to generate a relay list.
How the attack works
For the attack to be successful, a user or a process on the network needs to trigger an LLMNR or NBT-NS query that Responder can respond to, capturing the hash and relaying it using ntlmrelayx. This might involve waiting for a user to mistype a network resource name or a hostname.
Generate a relay list with crackmapexec
The first step in order to perform a successful relay attack, you will need a list of valid targets. Focusing on smb, this can be achieved via using the generate relay list flag. The list will be saved in the targets.txt file specific in the command below.
cme smb <CIDR> --gen-relay-list targets.txtDownload and Install Responder
Typically responder comes pre-installed on many penetration testing distributions, like Kali Linux or Parrot OS. If it’s not installed, you can clone it from GitHub:
git clone https://github.com/lgandx/Responder.gitConfigure Responder
Edit the Responder configuration file (Responder.conf) to enable or disable specific settings according to the network environment and your specific goals. In most cases, in an internally networked environment, SMB will be a primary target. Turn off the SMB and HTTP servers using the configuration file.
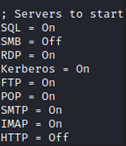
Run Responder
Execute Responder in your local network, specifying the interface to listen on:
python Responder.py -I eth0 --rdwThis command runs Responder on the eth0 interface, enables both LLMNR and NBT-NS poisoning, and logs hashes to the disk.
Setting up ntlmrelayx
Once Responder is running and capturing NTLM hashes, you can use ntlmrelayx to relay these credentials to authenticate to the target machines.
ntlmrelayx.py -tf targets.txtMonitoring and exploiting
Monitor both Responder and ntlmrelayx for successful captures and relays. Upon successful exploitation, you may have the ability to execute commands or access resources on the target machine as the authenticated user.
Key Characteristics:
- Unauthorised retransmission or delay of valid data transmission
- Often targets authentication communications
- Defended against with unique session tokens, timestamps, and nonce values
- Can be executed using tools like ‘ntlmrelayx’ part of the Impacket suite
Examples:
- Real-World Example: An attacker intercepts a user’s authentication token on an unsecured wireless network and uses it to gain access to a secured resource without the user’s knowledge, hours after the original token was sent.
- Hypothetical Scenario: Using ‘ntlmrelayx’, an attacker relays NTLM credentials sent by a user to authenticate to a file server, providing access to sensitive corporate documents without having to crack or guess a password.
Related Terms:
- Nonce: A random value that is generated for a specific session or transaction to prevent replay attacks.
- NTLM Authentication: A challenge-response authentication protocol used by Microsoft, which can be vulnerable to relay and replay attacks if not properly secured.
- Challenge-Response Authentication: An authentication mechanism where the user presents a response to a challenge (e.g., a password), with safeguards against replay attacks.
- Impacket: A collection of Python classes and tools for working with network protocols, often used in penetration testing and network attacks.
Learn better by watching a video? Here is a YouTube video explaining the concept of replay attacks.
